Overview of the most common areas of application
SPSA the Zero Trust Access solution for RDP environments, SSH access and for isolating insecure legacy systems via RDP or VNC connections.
Fast implementation through on-premise solutions “out of the box”. SPSA can be installed quickly and cost-effectively as a virtual appliance from VMware ESX 7.0 or as a physical appliance on a dedicated system.
The Zero Trust solution is supplemented by a secure patch infrastructure from Skillplan GmbH for the appliance operating system and SPSA.
| Abbreviation | Meaning |
| rdp | Remote Desktop Protocol for remote access to Windows systems |
| ssh | Secure shell for remote access to Linux/Unix systems, appliances and network components |
| SPSA Portal | User and administration portal of the SPSA environment |
| SPSA Proxy | Proxy component for protocol conversion for SPSA |
Access to a compromised network
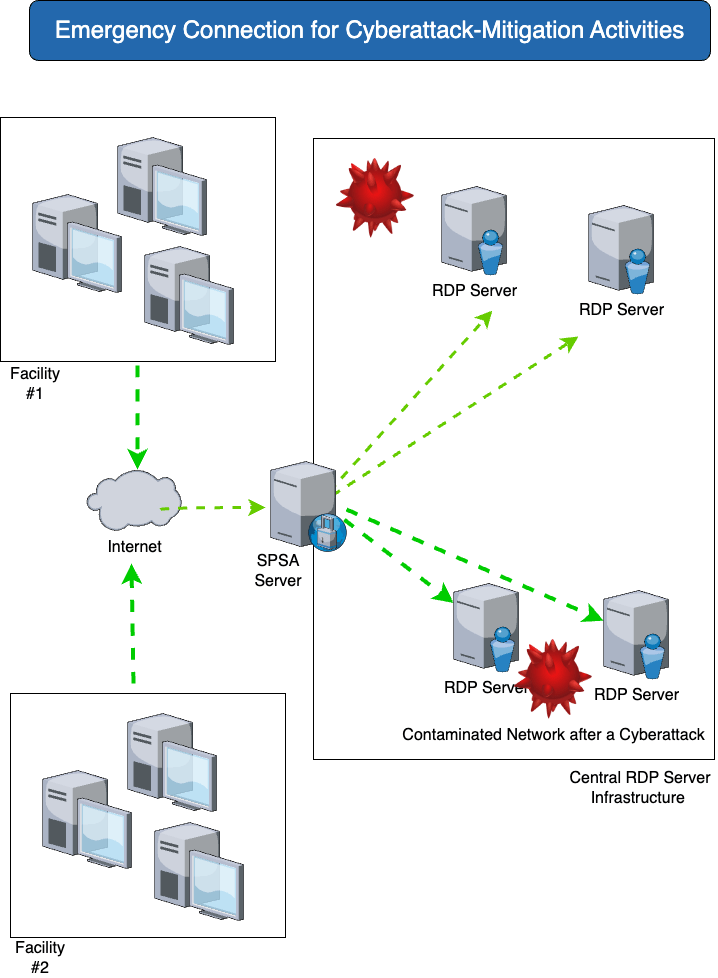
| You need | The solution with SPSA |
Secure access to compromised networks from a “secure” network. Access should be made possible so that production-relevant IT can be used again as soon as possible. | SPSA enables access to production systems in contaminated networks without jeopardizing the ongoing rebuilding of the company’s IT infrastructure. |
Secure access to legacy systems
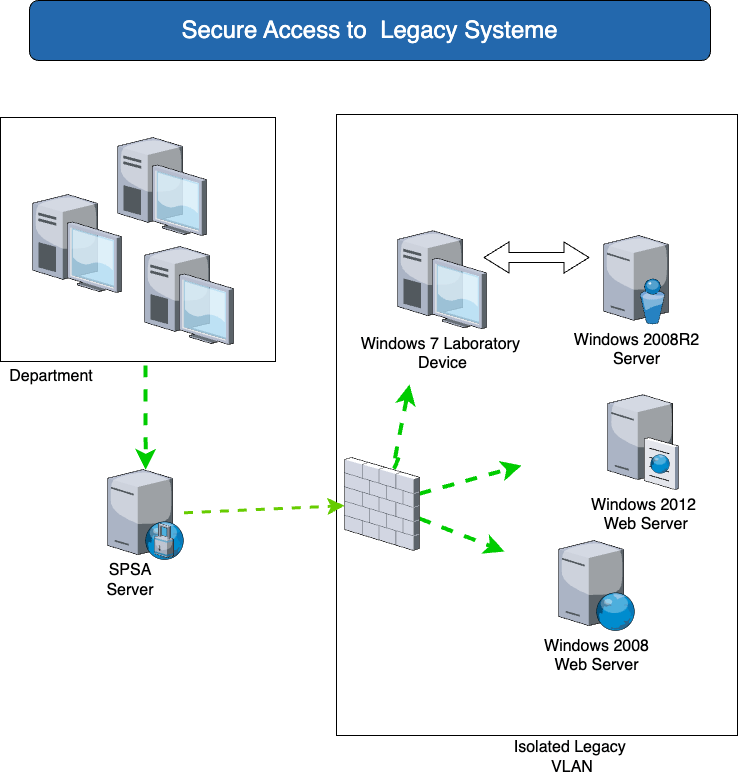
| You need | The solution with SPSA |
| The operation of isolated legacy systems, even with known zero-day gaps, without exposing these systems. Risk minimization in the event of unrecoverable security gaps. | Systems that can no longer be patched and systems with known security vulnerabilities can be isolated from the rest of the network and still be accessed without exposing the entire network. Functions such as cut & paste or file transfer can be controlled granularly on a system and user basis, right down to pure display sharing without access to the system. Examples are: Access via RDP to Windows Server 2008 applications or Windows 7 applications, which cannot yet be replaced. |
Securing existing RDP servers
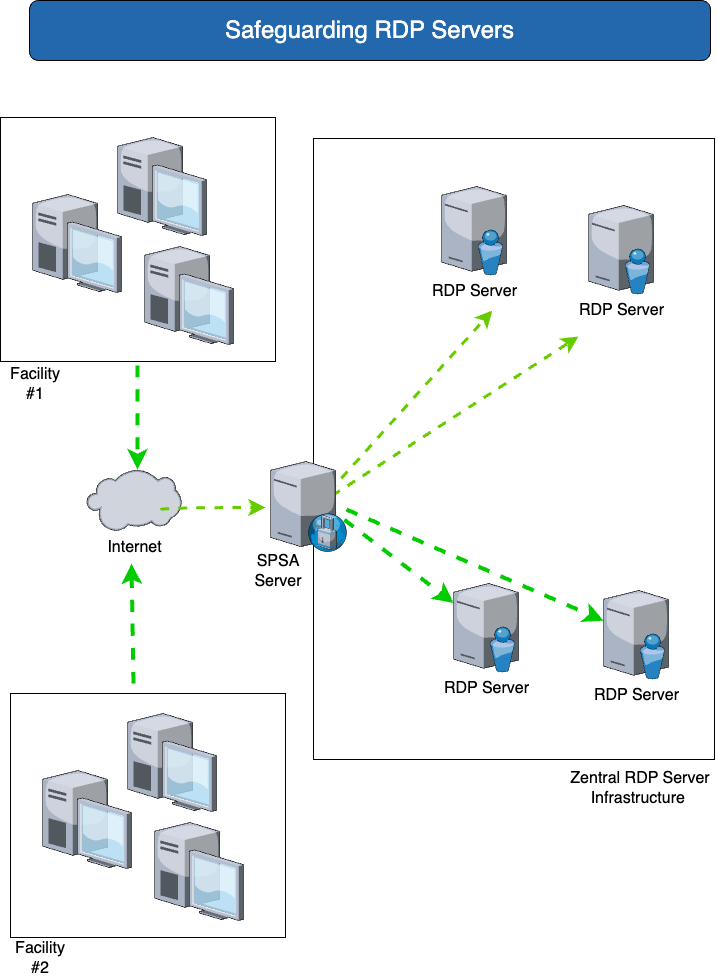
| You need | The solution with SPSA |
| The existing RDP installations are to be secured in order to minimize the risk from the exploitation of RDP servers in the network. | SPSA prevents lateral movement through a central access portal for server access via RDP. This enables SPSA to provide secure access to RDP servers for both internal and external access. |
Securing OT networks
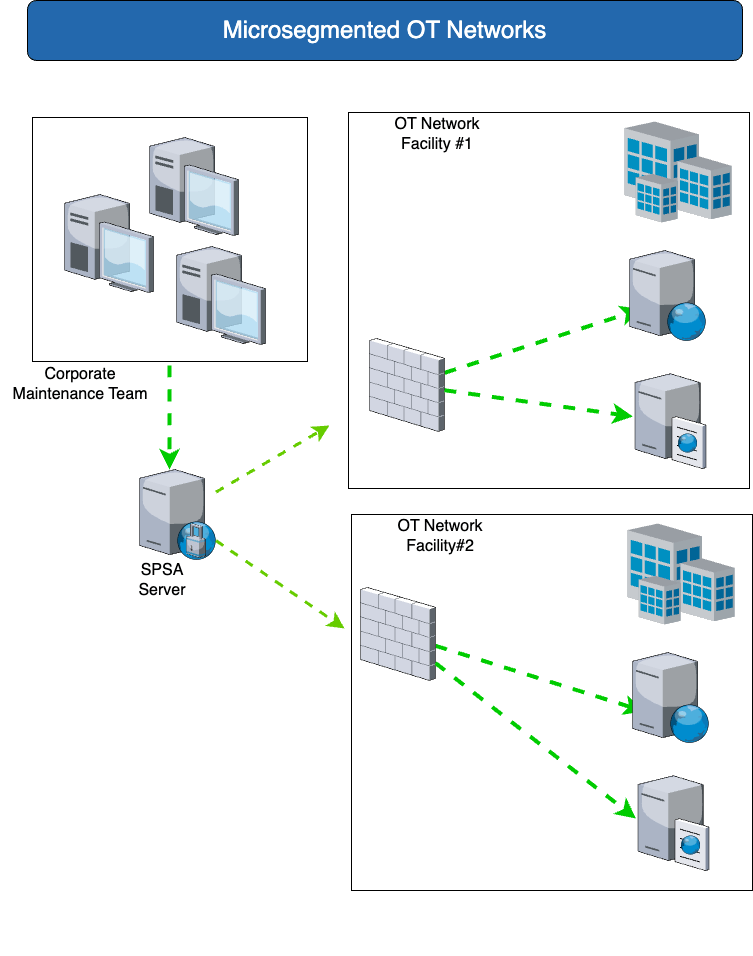
| You need | The solution with SPSA |
| Gesicherte Zugriffe bei Segmentierung von Produktionsnetzwerken, Labornetzten und OT Netzwerken soll aus Office-Netzwerken ermöglicht werden (ohne die Segmentierung aufzuheben). | If OT and IT networks are to be operated separately (micro-segmentation), the use of SPA enables secure access from the IT network to systems in OT networks via a central access portal. |
Remote Maintenance
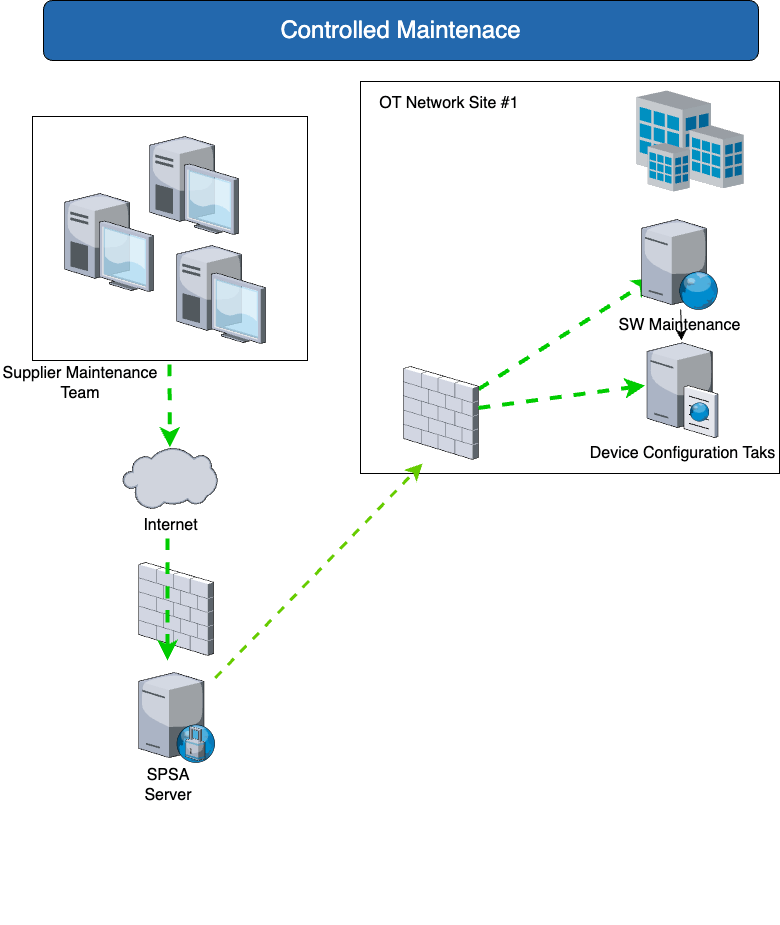
| You need | The solution with SPSA |
| For maintenance purposes, support technicians must be able to access internal systems via the Internet. RDP, ssh or Telnet connections are used for this. Individual employees of acquired companies should be able to access selected systems quickly via the Internet in order to speed up the integration process. | Enables time-controlled access by suppliers to systems for maintenance purposes (without installation of additional software at the suppliers) for access via ssh, RDP and VNC. SPSA enables access to server systems for suppliers or for employees of companies that are not connected to the company network via a Managed Remote Maintenance Gateway. |
Central Privileged Access instance for the administration of MS servers
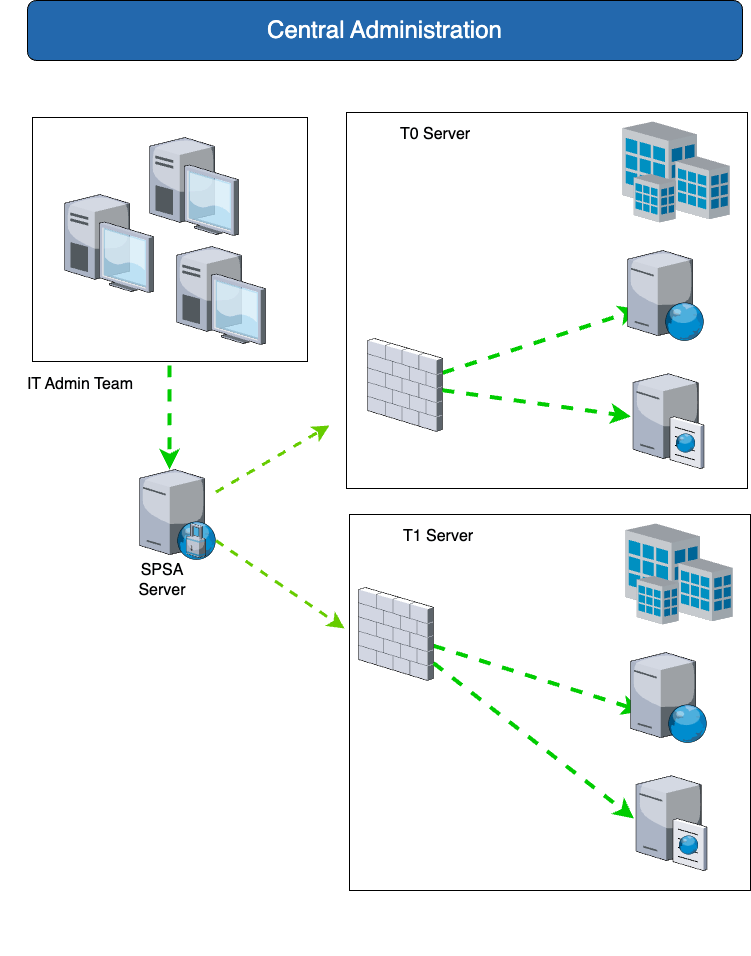
| You need | The solution with SPSA |
| As part of securing the Active Directory and business-critical applications based on MS Windows, the administration is to be centralized and secured. Furthermore, active directories, which are secured according to the MS Tiering model, are to be additionally secured by central administration portals. | For securing administrative connections in the management of Tier0, Tier1 and Tier2 systems when introducing the Microsoft tiering model (central provision of the PAW infrastructure). SPSA enables the central management of administrative access to critical infrastructure components. This can be combined with the MS tiering model. In addition, SPA enables centralized logging of privileged access to critical infrastructure servers via RDP or ssh. |
SPSA Features
Secure & proven software based on Apache GuacamoleTM
- A secure system with Lowest Privileged Access
- A secure update and patching infrastructure that keeps your compliance up-to-date
- Simple admin interface for managing the appliance
- Integrated option to create and store backups of critical data
- Integrated performance monitoring with the option of uploading the monitoring data to Skillplan GmbH for evaluation
- Support for RDP, SSH, telnet and VNC connections
- Integrated user database with MFA support for standard authentication apps such as Microsoft or Google Authenticator
- The option to limit user logins in terms of time
- Active Directory Single Sign-on (Pro Version)
- Azure Active Directory (SAML) Single Sign-on with integration of Conditional Access (Pro Version)
- Portal with up to 4 separate SPSA proxies at up to four locations (Pro version
- Recording and replay of RDP and SSH sessions via video recording (Pro version)
SPSA Next Steps
Would you like an SPSA performance?
Then please contact sales@skill-plan.com to arrange a demo appointment.
Would you like to try out SPSA during a 30-day trial period?
Then please contact sales@skill-plan.com to register for a test position
Do you have further questions and need individual answers?
Describe your questions to sales@skill-plan.com so that we can prepare for an appointment via Teams or Zoom.
