Cyberattacks – anyone can be affected
However, you can also prepare yourself.
At a time when the threat of cyberattacks is almost standard, it is essential that companies and organizations continuously update and adapt their security measures.
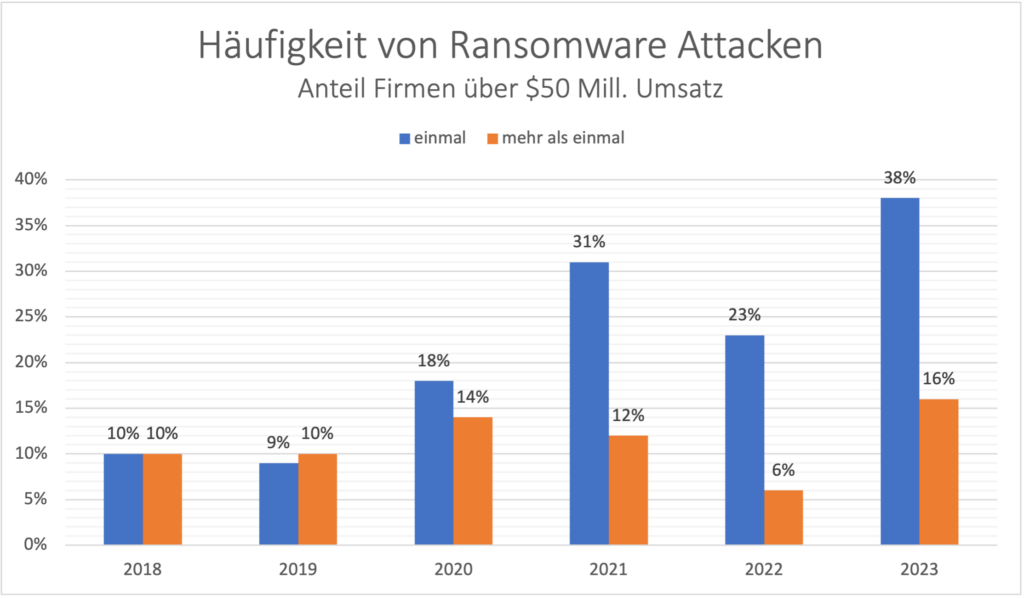
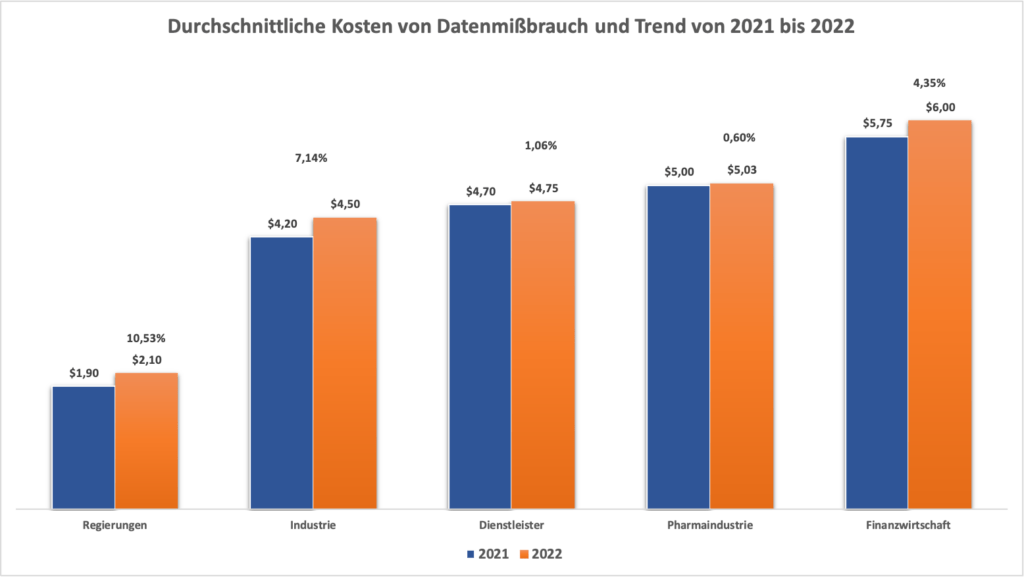
The frequency, but also the costs of recovery and downtime costs are increasing, especially in the public and industrial sectors.
Cyber attacks in figures
New malware variants in 2023 per day in Germany
Source: Statista, registered by the Federal Office for Information Security (BSI)
The rapid increase in new malware variants per day in Germany clearly shows that conventional virus protection programs are no longer sufficient to effectively combat the growing threat.
“Zero Trust” is a promising approach here
to improve the protection of sensitive data and systems and strengthen the overall security posture. By implementing the principle of “zero trust” and taking the necessary steps to apply zero trust, companies can take their digital security to a new level and effectively ward off potential threats.
The defense against cyber attacks
Our customers benefit from our experience in adapting existing IT infrastructures, which are based on “best practice” approaches and migrated to a “Zero Trust” compliant environment with the support of appropriate software products.
If technical measures, such as
- Next Generation Firewalls,
- XEDR systems,
- SIEM implementations,
- Microsegmentation and
- Zero Trust solutions
flanked by appropriately adapted operating processes, security against cyberattacks can be increased as part of a security architecture.
And the end user must also be educated and trained to understand security in the company as part of their daily work and to act accordingly.
Standardized security guidelines at all levels
Only through uniform security guidelines, a comprehensive security architecture and the necessary process adjustments for operating processes and corresponding optimization of IT-supported business processes can cybersecurity in the company be significantly improved. Implementation requires both technical expertise and experienced project management, including change management, in order to professionally implement the defined changes in the company.
Strengthen your incident response strategy.
- Check your safety measures using the checklist.
- Get an overview in good time and act protectively.
- Ensure that your company is optimally protected.
- Minimize the impact of cyberattacks.
- Maintain your legal capacity.
Skill-Plan Incident-Response:
Empowering Resilience, Ensuring Security!
Effective Incident Response Checklist
To receive the free download of the checklist, please fill in the following information. After successful entry you will receive immediate access to the pdf. checklist:
Preview of the checklist
